Introduction to Man-in-the-Middle (MITM) Attacks
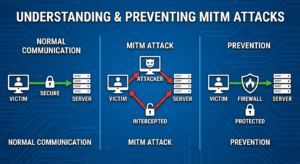
In the ever-evolving landscape of cybersecurity threats, Man-in-the-Middle (MITM) attacks remain one of the most insidious methods used by cybercriminals to intercept communications between two unsuspecting parties. Essentially, a MITM attack involves a hacker inserting themselves into a legitimate data exchange, enabling them to steal sensitive information or manipulate communications. Whether you’re connected to a public Wi-Fi network or navigating secure online services, the threat of digital spying through data interception is ever-looming.
An effective MITM attack can exploit encryption vulnerabilities, making even secure communications susceptible to breaches. Techniques such as SSL stripping or simple network eavesdropping are commonly employed to hijack data. As users increasingly rely on internet security measures, understanding this phenomenon becomes crucial. Awareness and proactive measures can significantly mitigate MITM attack risks, enhancing overall Wi-Fi security.
For individuals and organizations alike, exploring resources on related cybersecurity topics can offer valuable insights. For a broader understanding of internet security protocols, consider visiting our guide on What is a Firewall? A Beginner’s Guide to Cybersecurity. Furthermore, authoritative resources such as Kaspersky’s overview on MITM attacks provide in-depth information on how these cybersecurity threats operate and can be prevented.
Understanding How MITM Attacks Work
A Man-in-the-Middle (MITM) attack is a form of digital spying where an attacker secretly intercepts and relays communication between two parties who believe they are directly communicating with each other. By exploiting encryption vulnerabilities, the attacker can access sensitive data, leading to severe cybersecurity threats. This process typically involves network eavesdropping and can compromise your internet security by making your secure communications vulnerable to interception.
During a MITM attack, the perpetrator positions themselves between the victim and the destination server. They may use various tactics such as SSL stripping, modifying communications, or impersonating the server to deceive the victim into revealing private information. Public networks, like unsecured Wi-Fi, are particularly susceptible, and poor Wi-Fi security heightens the risk significantly.
Understanding how these attacks work is crucial for MITM attack prevention. By being aware of the methods used and recognizing the signs of a breach, individuals and organizations can implement stronger security measures. To further enhance your network protection, consider reading our guide on what is a firewall and how it fortifies your defenses.
For a more comprehensive understanding of MITM attacks and protective measures, visit the detailed resource on CSO Online.
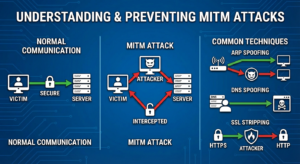
Common Techniques Used in MITM Attacks
Man-in-the-Middle (MITM) attacks are notorious cybersecurity threats that exploit vulnerabilities in network security to intercept data. Hackers employ a variety of techniques to carry out these attacks, making it essential for individuals and organizations to be aware of the methods involved in digital spying.
ARP Spoofing
One of the most common methods hackers use is ARP (Address Resolution Protocol) spoofing. This technique involves sending falsified ARP messages over a local network to associate the attacker’s MAC address with the IP address of a legitimate device. This allows the attacker to intercept, modify, or even stop data from reaching its intended destination, compromising secure communications.
DNS Spoofing
In DNS spoofing, attackers corrupt the DNS server or the resolver cache, redirecting users from legitimate websites to fraudulent ones. This can result in sensitive information, such as login credentials and financial details, being exposed to cybercriminals. Our comprehensive firewall guide can help enhance your network security.
SSL Stripping
SSL stripping downgrades a secure HTTPS connection to an unencrypted HTTP connection, enabling hackers to view and manipulate data transmitted between the client and server. This method exploits encryption vulnerabilities, making it crucial for users to remain vigilant about internet security. Learn more about avoiding such pitfalls by exploring SSL security articles, like those on Norton’s official site.
How Hackers Spy on Your Online Activities
Understanding how hackers spy on you through a Man-in-the-Middle (MITM) attack is crucial for safeguarding your internet security. In a typical MITM attack, hackers intercept communications between two parties to eavesdrop on your confidential data. This unauthorized access often occurs in poorly secured networks, making Wi-Fi security a high priority.
Hackers employ various techniques for network eavesdropping, such as exploiting encryption vulnerabilities or using SSL stripping to access unencrypted data. This type of cybersecurity threat can result in data interception, where sensitive information, like passwords and credit card numbers, is compromised.
Deploying robust MITM attack prevention tactics is essential. These include utilizing VPNs, ensuring HTTPS is always enabled, and maintaining updated software to protect against digital spying attempts. For a comprehensive understanding of protecting your data online, you can also explore topics like password protection strategies and other prevention techniques.
For more detailed explanations on Man-in-the-Middle attacks, consider visiting reputable sources such as Kaspersky to enhance your knowledge of secure communications.
Real-World Examples of MITM Attacks
Man-in-the-Middle (MITM) attacks are a pervasive cybersecurity threat that leverage network eavesdropping to intercept or manipulate communications. One infamous real-world example is the ‘SSL stripping’ attack, which exploits encryption vulnerabilities in secure communications. Typically, attackers intercept communications between a user and a website, downgrading HTTPS connections to the less secure HTTP, thereby accessing sensitive information like login credentials.
Public Wi-Fi networks are particularly vulnerable to digital spying and MITM attacks. At airports and cafes, malicious actors can create fake Wi-Fi hotspots that look legitimate. Unsuspecting users connect and unknowingly allow attackers to intercept data and potentially infect systems with malware. Wi-Fi security measures such as VPNs can help mitigate this risk.
Another instance involves mobile banking applications. Cybercriminals can inject themselves between mobile apps and banks’ servers to perform data interception. This allows unauthorized parties to siphon off private data or initiate fraudulent transactions.
Understanding and preventing these attacks is crucial for maintaining Internet security. Considering other cybersecurity threats such as social engineering, you may also explore our comprehensive guide on preventing social engineering. For more detailed information on MITM attacks, Kaspersky’s Resource Center offers an extensive overview.
Identifying the Signs of a MITM Attack
A Man-in-the-Middle (MITM) attack can be difficult to detect, as cybercriminals subtly eavesdrop on communications. However, recognizing the signs early is crucial for safeguarding against these network eavesdropping techniques. MITM attacks can manifest through numerous symptoms, each related to the breakdown of secure communications.
An unexpected warning from your browser, such as an untrusted SSL certificate, often indicates an active attack. This usually results from hackers attempting SSL stripping to weaken encryption. Another sign includes frequent disconnections or unexplained poor Wi-Fi security performance. If websites or applications begin to display odd URLs or unexpected pop-ups, it’s another black mark suggesting data interception.
Monitoring network traffic for unusual patterns can also reveal potential digital spying efforts. If you notice unknown devices on your network or unanticipated bandwidth consumption, it may be worth investigating deeper. By understanding these signs, you bolster your defenses against these pressing cybersecurity threats.
For more robust protection, consider exploring the basics of firewalls and how they can protect your network from such vulnerabilities.
For a comprehensive breakdown of MITM attacks and how they function, you can visit this detailed guide on MITM attacks by Norton.
The Impact of MITM Attacks on Personal and Business Security
Man-in-the-Middle (MITM) attacks pose significant threats to both personal and business security by facilitating unauthorized data interception. These attacks can lead to severe consequences such as identity theft, credential compromise, and substantial financial losses. As a form of network eavesdropping, MITM attacks exploit encryption vulnerabilities, enabling hackers to engage in digital spying and undermine secure communications.
For businesses, the impact of an MITM attack can ripple throughout the organization. Sensitive customer data might be exposed, resulting in loss of trust and potential legal ramifications. Additionally, MITM attacks can jeopardize an organization’s Wi-Fi security, compromising entire networks. Implementing robust MITM attack prevention strategies, such as using SSL to avoid SSL stripping and maintaining up-to-date internet security measures, is vital to safeguarding against these cybersecurity threats.
On a personal level, individuals face increased risks such as unauthorized access to online banking accounts and other private data. Strengthening personal cybersecurity through use of reliable encryption and secure connections minimizes exposure to these dangers. For further reading on protecting online identities and associated technologies, explore our comprehensive guide on online identity security.
For an in-depth understanding of MITM attacks, you can visit this authoritative resource by Cisco.
How to Protect Yourself from MITM Attacks
As cybersecurity threats continue to evolve, safeguarding your interactions from a Man-in-the-Middle (MITM) attack is essential. MITM attacks can lead to data interception and unauthorized access to personal information. Here’s how you can enhance your internet security to prevent network eavesdropping and digital spying.
Use Secure Networks
Avoid using public Wi-Fi for transactions or accessing sensitive information. When possible, connect through a Virtual Private Network (VPN) to encrypt your data and reduce encryption vulnerabilities associated with open networks. For more information on Wi-Fi security, consider reading about fixes for slow Wi-Fi issues here.
Enable HTTPS
Ensure websites that require login credentials use HTTPS. This protocol encrypts data between the server and your browser, thwarting potential data interception. Be wary of SSL stripping attacks, which downgrade your connection from HTTPS to HTTP.
Strong Authentication
Implement two-factor authentication (2FA) where possible. This adds an extra layer of security even if your password is compromised. Refer to external resources such as the CSO Online guide for detailed information on MITM attacks.
Regular Software Updates
Keep operating systems, firewalls, and security software updated to patch any potential vulnerabilities that could be exploited for digital spying. For detailed insights into cybersecurity fundamentals, you might find it helpful to explore our guide on firewalls.
By adopting these strategies, you can significantly enhance your protection against MITM attack prevention efforts, ensuring more secure communications in your daily digital life.
Tools and Technologies to Prevent MITM Attacks
To combat the ever-evolving threat of Man-in-the-Middle (MITM) attacks, using advanced tools and technologies for MITM attack prevention is essential. Here, we explore effective strategies to enhance your network eavesdropping defenses and secure communications.
Firstly, employing end-to-end encryption is crucial. This ensures that even if data interception occurs, the intercepted information remains unreadable. Many modern messengers and websites utilize this to guard against digital spying. Additionally, using protocols like HTTPS can prevent cybercriminals from executing SSL stripping attacks and compromising internet security.
Regularly updating and patching your systems can close encryption vulnerabilities that attackers might exploit. A personal or corporate firewall also plays a vital role in your cybersecurity toolkit. To learn more about how firewalls contribute to cybersecurity, visit our guide on what is a firewall.
Public Wi-Fi networks are notorious for hosting MITM threats. Implementing a robust Virtual Private Network (VPN) can secure your data on such networks, enhancing Wi-Fi security. Lastly, awareness and training can arm users against social engineering tactics that often precede MITM attacks.
For further reading on the complexities and defenses against MITM attacks, check out Kaspersky’s detailed resource.
Stay Safe Online: Best Practices Against MITM Attacks
In an era where cybersecurity threats like a Man-in-the-Middle (MITM) attack are increasingly prevalent, adopting robust online security practices is vital. Ensuring internet security involves several proactive measures that can help safeguard against data interception and digital spying.
To enhance MITM attack prevention, begin by securing your Wi-Fi network with a strong, unique password. Opt for WPA3 encryption, which offers better protection against network eavesdropping. Regularly update your router firmware to fix encryption vulnerabilities.
Utilizing VPNs adds an extra layer of security for communications over public networks. VPNs encrypt your data, making it difficult for attackers to breach your secure communications. It’s also crucial to only access websites with HTTPS; these sites encrypt data to prevent SSL stripping attacks.
Modern web browsers usually alert you to suspicious websites and untrusted certificates. Be attentive to these warnings as they play a critical role in MITM attack prevention. For more on how to tighten your digital defenses, explore our guide on firewall basics.
For further reading on MITM attacks and how hackers spy on your information, check out this comprehensive guide on Kaspersky’s official site.
The Future of Cybersecurity and Mitigating MITM Threats
The horizon of cybersecurity is evolving, with enhanced measures to combat the growing menace of Man-in-the-Middle (MITM) attacks. As digital ecosystems grow, the need for robust Internet security becomes paramount. In this section, we explore the future of cybersecurity and strategies to mitigate MITM threats.
Cybersecurity threats continue to evolve with hackers becoming more sophisticated in their methods of digital spying and data interception. Traditional network eavesdropping techniques are being replaced by advanced methods that exploit encryption vulnerabilities. To combat this, organizations must prioritize secure communications by adopting cutting-edge encryption protocols and SSL stripping countermeasures.
Beyond technical solutions, raising awareness around Wi-Fi security and promoting best practices for safe internet usage are crucial. Understanding the role of firewalls can also enhance an organization’s defense against such attacks.
- Implement end-to-end encryption to secure information traffic.
- Encourage HTTPS adoption to thwart MITM attacks.
- Leverage AI-driven threat detection systems for real-time defense.
For more comprehensive insights, resources like Kaspersky’s guide on MITM attacks provide valuable information. As tech landscapes develop, a proactive approach in cybersecurity will be indispensable in safeguarding digital futures.
Conclusion: The Importance of Being Vigilant Against MITM Attacks
In an era where cybersecurity threats are increasingly sophisticated, understanding the mechanics of a Man-in-the-Middle (MITM) Attack is crucial. These attacks, involving digital spying and data interception, threaten the privacy and security of our communications across the internet. MITM attack prevention should be at the forefront of any security strategy, as such attacks expose encryption vulnerabilities, often through methods like SSL stripping and network eavesdropping.
To maintain robust internet security, it’s essential to adopt comprehensive measures ranging from employing secure communications to enhancing Wi-Fi security. Educating yourself on internet security is vital, as is keeping abreast with evolving strategies to thwart these cybersecurity threats. For further insights into protecting your data, explore our guide on social engineering and how to prevent it.
Vigilance in recognizing the signs of potential attacks and proactive defense strategies, such as using updated encryption protocols and ensuring strong network hygiene, are imperative. To learn more about protecting yourself, consider delving into resources like the Kaspersky Resource Center for expert advice.